As we all know SQL Server 2005 Express is a very powerful free edition of SQL Server 2005. However it does not contain SQL Server Agent service. Because of this scheduling jobs is not possible. So if we want to do this we have to install a free or commercial 3rd party product. This usually isn't allowed due to the security policies of many hosting companies and thus presents a problem. Maybe we want to schedule daily backups, database reindexing, statistics updating, etc. This is why I wanted to have a solution based only on SQL Server 2005 Express and not dependent on the hosting company. And of course there is one based on our old friend the Service Broker.
Monday, December 29, 2008
Scheduling Jobs in SQL Server Express - SQLTeam.com
As we all know SQL Server 2005 Express is a very powerful free edition of SQL Server 2005. However it does not contain SQL Server Agent service. Because of this scheduling jobs is not possible. So if we want to do this we have to install a free or commercial 3rd party product. This usually isn't allowed due to the security policies of many hosting companies and thus presents a problem. Maybe we want to schedule daily backups, database reindexing, statistics updating, etc. This is why I wanted to have a solution based only on SQL Server 2005 Express and not dependent on the hosting company. And of course there is one based on our old friend the Service Broker.
Friday, December 26, 2008
CodeProject: GD library wrapper
GD library wrapper (for ASP developers with PHP vs ASP examples).
Download source - 998 Kb
Response.ContentType = "image/png";
var gdImage = Server.CreateObject("GDLibrary.gdImage");
gdImage.Create(230, 20);
gdImage.ColorAllocate(0, 10, 10);
var TextColor = gdImage.ColorAllocate(233, 114, 191);
gdImage.Chars(gdImage.FontGetLarge(), 5, 5,
"My first Program with GD", TextColor);
Response.BinaryWrite(gdImage.ToPngStream().Read);
CodeProject: Implement Phonetic ("Sounds-like") Name Searches with Double Metaphone
Presents a C# implementation of Double Metaphone, for use with any of the .NET languages.
Double Metaphone Part I: Introduction & C++ Implementation
Double Metaphone Part II: Visual Basic and Relational Database Solutions
Double Metaphone Part III: VBScript and ASP & Database Solutions
Double Metaphone Part IV: SQL Server and Advanced Database Topics
Double Metaphone Part V: .NET Implementation
Double Metaphone Part VI: Other Methods & Additional Resources
Double Metaphone Algorithmus in TSQL
Convert the C++ Double Metaphone algorithm to T-SQL
26094.zip
Longest common substring - Code Snippets - Wikibooks
Public Function LongestCommonSubstring(ByVal s1 As String, ByVal s2 As String) As Integer
Dim num(s1.Length - 1, s2.Length - 1) As Integer '2D array
Dim letter1 As Char = Nothing
Dim letter2 As Char = Nothing
Dim len As Integer = 0
Dim ans As Integer = 0
For i As Integer = 0 To s1.Length - 1
For j As Integer = 0 To s2.Length - 1
letter1 = s1.Chars(i)
letter2 = s2.Chars(j)
If Not letter1.Equals(letter2) Then
num(i, j) = 0
Else
If i.Equals(0) Or j.Equals(0) Then
num(i, j) = 1
Else
num(i, j) = 1 + num(i - 1, j - 1)
End If
If num(i, j) > len Then
len = num(i, j)
ans = num(i, j)
End If
End If
Next j
Next i
Return ans
End Function
Levenshtein distance - Code Snippets - Wikibooks
VBA (with Damerau extension)
This VBA version uses recursion and a maximum allowed distance. The analysis to identify quasi-duplicated strings or spelling mistakes can be narrowed down to a corridor in the result matrix. The Damerau extension has also been added to the Levenshtein algorithm.
Function damerau_levenshtein(s1 As String, s2 As String, Optional limit As Variant, Optional result As Variant) As Integer
'This function returns the Levenshtein distance capped by the limit parameter.
'Usage : e.g. damerau_levenshtein("Thibault","Gorisse") to get the exact distance
' or damerau_levenshtein("correctly written words","corectly writen words",4) to identify similar spellings
Dim diagonal As Integer
Dim horizontal As Integer
Dim vertical As Integer
Dim swap As Integer
Dim final As Integer
'set a maximum limit if not set
If IsMissing(limit) Then
limit = Len(s1) + Len(s2)
End If
'create the result matrix to store intermediary results
If IsMissing(result) Then
Dim i, j As Integer ' pointeur
ReDim result(Len(s1), Len(s2)) As Integer
End If
'Start of the strings analysis
If result(Len(s1), Len(s2)) <>= limit Then
final = limit
Else
If Len(s1) = 0 Or Len(s2) = 0 Then
'End of recursivity
final = Len(s1) + Len(s2)
Else
'Core of levenshtein algorithm
If Mid(s1, 1, 1) = Mid(s2, 1, 1) Then
final = damerau_levenshtein(Mid(s1, 2), Mid(s2, 2), limit, result)
Else
If Mid(s1, 1, 1) = Mid(s2, 2, 1) And Mid(s1, 2, 1) = Mid(s2, 1, 1) Then
'Damerau extension counting swapped letters
swap = damerau_levenshtein(Mid(s1, 3), Mid(s2, 3), limit - 1, result)
final = 1 + swap
Else
'The function minimum is implemented via the limit parameter.
'The diagonal search usually reaches the limit the quickest.
diagonal = damerau_levenshtein(Mid(s1, 2), Mid(s2, 2), limit - 1, result)
horizontal = damerau_levenshtein(Mid(s1, 2), s2, diagonal, result)
vertical = damerau_levenshtein(s1, Mid(s2, 2), horizontal, result)
final = 1 + vertical
End If
End If
End If
End If
Else
'retrieve intermediate result
final = result(Len(s1), Len(s2)) - 1
End If
'returns the distance capped by the limit
If final < limit Then
damerau_levenshtein = final
'store intermediate result
result(Len(s1), Len(s2)) = final + 1
Else
damerau_levenshtein = limit
End If
End Function
Monday, December 22, 2008
Google’s Top 10 Hidden Treasures | MakeUseOf.com
about:internets
about:stats
about:memory
about:network
about:histograms
about:dns
about:cache
about:plugins
about:version
Wednesday, December 17, 2008
DHTML routines and functions
AJAX file upload
How to upload files using AJAX, without reloading the page? Read about the cross browser method to upload files using AJAX in only 1Kb of code.
Read more...
Scrollable HTML table
Scrollable HTML table JavaScript code can be used to convert tables in ordinary HTML into scrollable ones. No additional coding is necessary.
Read more...
Javascript context menu
Javascript context menu is very lightweight, OOP based and item-specific. You can attach this context menu to multiple containers. Read more...
Sortable HTML table
Sortable HTML table JavaScript code can be used to convert tables in ordinary HTML into sortable ones. This script is unobtrusive. No additional coding is necessary.
Read more...
Javascript drag and drop
Javascript drag and drop will enable you to drag elements on your page. You can attach this drag and drop handler to any relative or absolute positioned element.
Read more...
Javascript custom cursor
Cross hair mouse cursor. Learn ho to add a fancy custom cursor to your website using Javascript.
Read more...
Javascript pie menu
Javascript pie menu allows you to build an configurable context pie menu.
Read more...
Unselectable text
A method to have unselectable text in a browser. Script makes text in an HTML page unselectable by visitors.
Read more...
A method to have unselectable text in a browser. Script makes text in an HTML page unselectable by visitors.
Read more...
Javascript routines and functions
Javascript trim
Javascript trim is a string function. It will trim all leading and trailing occurrences of whitespace characters.
Read more...
Javascript string replace
Javascript string replace is a very useful function. Javascript has a built-in string replace function but it uses regular expressions.
Read more...
Javascript sprintf
Javascript sprintf implementation. This Javascript function returns a string formatted by the usual printf/sprintf conventions. Read more...
Javascript url decode, encode
You can use this Javascript to encode / decode url parameters. Script is fully compatible with UTF-8 encoding. Read more...
Javascript MD5
This Javascript is used to calculate MD5 hash of a string. MD5 is a widely-used cryptographic hash function with a 128-bit hash value.
Read more...
Javascript SHA-1
This Javascript is used to calculate SHA-1 hash of a string. The Secure Hash Algorithm is one of the many cryptographic hash functions. Read more...
Javascript SHA-256
SHA-256 Javascript implementation is used to process variable length message into a fixed-length output using the SHA256 algorithm.
Read more...
Javascript CRC32
CRC32 function generates the cyclic redundancy checksum polynomial of 32-bit lengths of the string.
Read more...
Javascript base64 encoding
This base64 Javascript is used to encode / decode data using base64 encoding. This Javascript is fully compatible with UTF-8 encoding. Read more...
Javascript UTF-8
Use this Javascript to encode decode UTF-8 data. UTF-8 is a variable-length character encoding for Unicode.
Read more...
Javascript pad
Pad is a string manipulation function. Javascript pad implementation pads a string to a certain length with another string.
Read more...
Javascript cookies
Javascript cookies object with methods to save, read and erase them. Using these methods you can manipulate cookies on your site.
Read more...
Sunday, November 9, 2008
AVIFile Tutorial
Introduction and Preparation
Step 1 - Getting a Handle on AVIsOpening And Closing Existing AVI FilesCreate a sample program that allows the user to choose an AVI file from the disk and get an interface pointer to it for use with the AVIFile functions. This is the framework sample which is built on in all the other steps. Be sure you understand it before going on.
Step 2 - Gently down the StreamsWorking With Existing StreamsCreate a sample program that gets a pointer to the existing video stream in an AVI file and returns information about the stream.
Step 3 - AVI to BMPsWorking With Existing FramesCreate a utility that gets each frame from the video stream in an AVI file and saves it to a bitmap file.
Step 4 - Recompress your videosCreating New AVI Files From StreamsCreate a utility that copies the video stream from any AVI file, recompresses it using whatever codec the user chooses and saves it to a new AVI file.
Step 5 - BMPs to AVICreating New AVI Files From Bitmap FilesCreate a utility that gets a list of bitmap files from the user and creates a new AVI file from them using a specified frame rate.
Friday, November 7, 2008
Thursday, September 18, 2008
MEncoder - crf - qp - bitrate usage examples
MEncoder Sherpya-SVN-r27323-4.2.4 (C) 2000-2008 MPlayer Team
CPU: Intel(R) Core(TM)2 Duo CPU T9300 @ 2.50GHz (Family: 6, Model: 23, Stepping: 6)
CPUflags: Type: 6 MMX: 1 MMX2: 1 3DNow: 0 3DNow2: 0 SSE: 1 SSE2: 1
constant quantizer:
MEncoder.exe -sws 9 -vf crop=640:272:0:0,scale -ovc x264 -x264encopts frameref=6:bframes=3:me=3:subq=7:brdo:deblock:deblockalpha=0:deblockbeta=0:bime:b_adapt:cabac:b_pyramid:weight_b:mixed_refs:chroma_me:trellis=1:i4x4:i8x8:8x8mv:b8x8mv:4x4mv:8x8dct:nopsnr:qp=22 -oac mp3lame -lameopts cbr:br=96:aq=0 -noskip -priority belownormal -of avi -o "x264.avi" "hn.avi"
constant quality:
MEncoder.exe -sws 9 -vf crop=630:270:10:0,scale -ovc x264 -x264encopts frameref=6:bframes=3:me=3:subq=7:brdo:deblock:deblockalpha=0:deblockbeta=0:bime:b_adapt:cabac:b_pyramid:weight_b:mixed_refs:chroma_me:trellis=1:i4x4:i8x8:8x8mv:b8x8mv:4x4mv:8x8dct:nopsnr:crf=22 -oac mp3lame -lameopts cbr:br=96:aq=0 -noskip -priority belownormal -of avi -o "x264.avi" "hn.avi"
constant bitrate, 1st pass:
MEncoder.exe -sws 9 -vf crop=640:272:0:0,scale -ovc x264 -x264encopts frameref=6:bframes=3:me=3:subq=7:brdo:deblock:deblockalpha=0:deblockbeta=0:bime:b_adapt:cabac:b_pyramid:weight_b:mixed_refs:chroma_me:trellis=1:i4x4:i8x8:8x8mv:b8x8mv:4x4mv:8x8dct:nopsnr:bitrate=700:pass=1:turbo=1 -nosound -noskip -priority belownormal -passlogfile "D:\m\jd\data\Achterbahn.x264.avi.stats" -of avi -o "x264.avi" "hn.avi"
constant quality and bitrate:
mencoder -ovc x264 -x264encopts crf=18:subq=6:partitions=all:8x8dct:me=umh:frameref=5:bframes=3:b_pyramid:weight_b:threads=auto:bitrate=700 -oac copy -o 18-700.avi "-XviD.avi"
MEncoder264 v1.1.9
-qp means : give me the quality I asked for, no matter how many bits it needs (same quantizer for all frames).
-crf does the same, but instead of choosing a quantizer for each frame, it determines a "visual perception" factor (based on the initial QP you specified), and once again, it means "give me the visual quality I asked for, no matter how many bits it needs".
What's the difference between Constant Quantizer and Constant Quality
These two modes are variations on the generic idea of "unknown filesize/bitrate, known quality" where the encoder aims to encode to a specified quality level. This is opposed to the normal "known bitrate/filesize, unknown quality" model where the encoder is given an average bitrate and must produce the best file possible with that. The advatage of the former is obviously that the quality can be precisely set, while the latter allows precise filesize control. Which one is right for you is your decision. Note that a 2pass encode to the same bitrate will look better.
In x264, there are two modes of "known quality", Constant Quantizer (CQ) and Constant Quality (aka CRF, Constant Ratefactor).
* Constant quantizer: every frame is encoded with a mathematically identical quantizer. Constant quantizerproduces a file that for the x264 program is of perfect constant quality (it would be 'interpreted' in a similar fashion by other video encoder programs).
* Constant quality (aka constant rate factor): the video is encoded to a nominal quantizer, but the encoder varies the quantizer on different frames to give a higher percieved quality for human eyes. The output will be the same size as a CQ encode, but it will look subjectively better to humans and is therefore generally the more used of these two modes.
CPU: Intel(R) Core(TM)2 Duo CPU T9300 @ 2.50GHz (Family: 6, Model: 23, Stepping: 6)
CPUflags: Type: 6 MMX: 1 MMX2: 1 3DNow: 0 3DNow2: 0 SSE: 1 SSE2: 1
constant quantizer:
MEncoder.exe -sws 9 -vf crop=640:272:0:0,scale -ovc x264 -x264encopts frameref=6:bframes=3:me=3:subq=7:brdo:deblock:deblockalpha=0:deblockbeta=0:bime:b_adapt:cabac:b_pyramid:weight_b:mixed_refs:chroma_me:trellis=1:i4x4:i8x8:8x8mv:b8x8mv:4x4mv:8x8dct:nopsnr:qp=22 -oac mp3lame -lameopts cbr:br=96:aq=0 -noskip -priority belownormal -of avi -o "x264.avi" "hn.avi"
constant quality:
MEncoder.exe -sws 9 -vf crop=630:270:10:0,scale -ovc x264 -x264encopts frameref=6:bframes=3:me=3:subq=7:brdo:deblock:deblockalpha=0:deblockbeta=0:bime:b_adapt:cabac:b_pyramid:weight_b:mixed_refs:chroma_me:trellis=1:i4x4:i8x8:8x8mv:b8x8mv:4x4mv:8x8dct:nopsnr:crf=22 -oac mp3lame -lameopts cbr:br=96:aq=0 -noskip -priority belownormal -of avi -o "x264.avi" "hn.avi"
constant bitrate, 1st pass:
MEncoder.exe -sws 9 -vf crop=640:272:0:0,scale -ovc x264 -x264encopts frameref=6:bframes=3:me=3:subq=7:brdo:deblock:deblockalpha=0:deblockbeta=0:bime:b_adapt:cabac:b_pyramid:weight_b:mixed_refs:chroma_me:trellis=1:i4x4:i8x8:8x8mv:b8x8mv:4x4mv:8x8dct:nopsnr:bitrate=700:pass=1:turbo=1 -nosound -noskip -priority belownormal -passlogfile "D:\m\jd\data\Achterbahn.x264.avi.stats" -of avi -o "x264.avi" "hn.avi"
constant quality and bitrate:
mencoder -ovc x264 -x264encopts crf=18:subq=6:partitions=all:8x8dct:me=umh:frameref=5:bframes=3:b_pyramid:weight_b:threads=auto:bitrate=700 -oac copy -o 18-700.avi "-XviD.avi"
MEncoder264 v1.1.9
-qp means : give me the quality I asked for, no matter how many bits it needs (same quantizer for all frames).
-crf does the same, but instead of choosing a quantizer for each frame, it determines a "visual perception" factor (based on the initial QP you specified), and once again, it means "give me the visual quality I asked for, no matter how many bits it needs".
What's the difference between Constant Quantizer and Constant Quality
These two modes are variations on the generic idea of "unknown filesize/bitrate, known quality" where the encoder aims to encode to a specified quality level. This is opposed to the normal "known bitrate/filesize, unknown quality" model where the encoder is given an average bitrate and must produce the best file possible with that. The advatage of the former is obviously that the quality can be precisely set, while the latter allows precise filesize control. Which one is right for you is your decision. Note that a 2pass encode to the same bitrate will look better.
In x264, there are two modes of "known quality", Constant Quantizer (CQ) and Constant Quality (aka CRF, Constant Ratefactor).
* Constant quantizer: every frame is encoded with a mathematically identical quantizer. Constant quantizerproduces a file that for the x264 program is of perfect constant quality (it would be 'interpreted' in a similar fashion by other video encoder programs).
* Constant quality (aka constant rate factor): the video is encoded to a nominal quantizer, but the encoder varies the quantizer on different frames to give a higher percieved quality for human eyes. The output will be the same size as a CQ encode, but it will look subjectively better to humans and is therefore generally the more used of these two modes.
Tuesday, September 9, 2008
NTFS-Compressor
SourceForge.net: NTFS-Compressor
This Program is designed to compress an NTFS-Harddisk with some Criteriums Microsoft does not make if you kompress a whole Drive * Files which are smaller than Clustersize are NOT compressed. * minimum Age of the Files to be compressed. * etc...
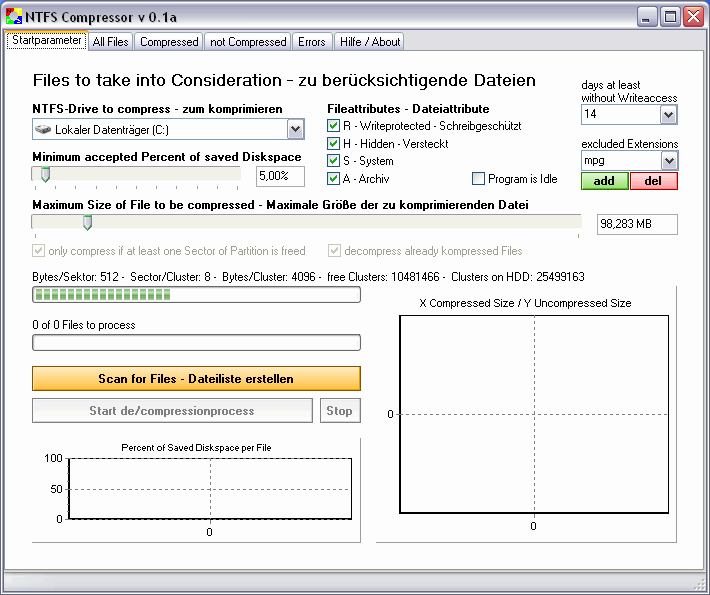
This Program is designed to compress an NTFS-Harddisk with some Criteriums Microsoft does not make if you kompress a whole Drive * Files which are smaller than Clustersize are NOT compressed. * minimum Age of the Files to be compressed. * etc...

Sunday, September 7, 2008
AVI-Mux GUI
AVI-Mux GUI
AVI-Mux GUI is an application that allows to combine several video, audio or subtitle files into one file, with out without size restriction, allowing to configure properties of the output file to a deeper level than usual for such applications.

AVI-Mux GUI is an application that allows to combine several video, audio or subtitle files into one file, with out without size restriction, allowing to configure properties of the output file to a deeper level than usual for such applications.

Tuesday, September 2, 2008
Malwarebytes.org
Malwarebytes is a site dedicated to fighting malware. Malwarebytes has developed a variety of tools that can identify and remove malicious software from your computer. When your computer becomes infected, Malwarebytes can provide the needed assistance to remove the infection and restore the machine back to optimum performance.
Malwarebytes' products have proven successful in removing malware from customers computers time and time again. Malwarebytes is constantly working on creating new products which are continuously updated to assist you in keeping your computer infection free.
Malwarebytes' Anti-Malware
Malwarebytes' Anti-Malware is an anti-malware application that can thoroughly remove even the most advanced malware. It includes a number of features, including a built in protection monitor that blocks malicious processes before they even start.
RogueRemover PRO
RogueRemover PRO is an application that can remove and protect you from rogue antispyware, antivirus, and hard drive cleaning applications with ease. It removes rogue applications such as WinAntiSpyware, AVSystemCare, and SpySheriff. The PRO version also includes a real-time monitor (RogueMonitor) which will alert you if you were to download a rogue application.
RogueRemover FREE
RogueRemover FREE is an application that can remove rogue antispyware, antivirus, and hard drive cleaning applications with ease. It removes rogue applications such as WinAntiSpyware, AVSystemCare, and SpySheriff.
FileASSASSIN
FileASSASSIN is an application that can delete locked malware files on your system. It uses advanced programming techniques to unload modules, close remote handles, and terminate processes to remove the file. Please use with caution as deleting critical system files may cause system errors.
RegASSASSIN
RegASSASSIN is a portable application which allows you to remove registry keys by resetting the keys' permissions and then deleting it. Please use with caution as deleting critical registry keys may cause system errors.
StartUpLite
StartUpLite is a lightweight application that will allow you to speed up your system startup. It provides a safe and efficient way to disable or remove unnecessary startup entries from your computer.
Qoofix
Qoofix is a removal tool which will remove the newest variants of Qoologic with the press of a button. Simply download the program, open it, and click Begin Removal.
E2TakeOut
E2TakeOut is a removal tool that targets and removees the E2Give and PTech malware with ease. Simply download the program, open it, and click Begin Removal.
AboutBuster
AboutBuster is an application that will detect the three most known variants of CWS.AboutBlank. Simply download the program, open it, and click Begin Removal. This application is also available in Spanish.
Network Analysis And Visualization
This is the new homepage for the Network Vizualization community. This community is focused on building libraries and applications. Additionally we will be focusing on addressing the issue of what file format to use. There are currently way too many, GraphML, GXL, GML and even SVG.
TTCP Utility
TtcpTx .NET V1.0.0.3
The .NET forms-based TTCP transmitter C# code was cleaned up by Matthew Armatis. His revision provides a vast improvement over the preliminary implementation by TFD.
PCATTCP V2.01.01.08
Sunday, August 31, 2008
NetMassDownloader
Mass Downloader For the .Net Framework which allows you do download .Net Framework source code in batch mode.The tool which enables offline debugging of .Net Framework in VS2008 (including Express Editions) , VS2005 (including Express Editions), and Codegear Rad Studio.
CodeProject: NetMassDownloader
With this tool you can download whole .Net Framework Source Code at once, and enjoy offline browsing With it , you can have whole the source code without any Visual Studio Product Installed.
http://www.codeplex.com/netmassdownloader (always latest version)
Socks Puppet - Socks 5 Server
Socks Puppet - Socks 5 Server
Socks Puppet is a multithreaded socks 5 server for Windows NT/2000/XP 98/ME.

Downloads:
Socks Puppet GUI: SocksPuppet-Setup.exe
Orginal Socks Puppet here: sockspuppet.zip
Check the readme here: readme.txt
Socks Puppet is a multithreaded socks 5 server for Windows NT/2000/XP 98/ME.

Downloads:
Socks Puppet GUI: SocksPuppet-Setup.exe
Orginal Socks Puppet here: sockspuppet.zip
Check the readme here: readme.txt
Thursday, August 28, 2008
XSLT Samples Viewer
The XSLT Samples Viewer 1.0 is a visual, interactive learning tool that provides sample XSLT style sheets for XSLT elements and functions, as well as XPath functions.
The Extensible Stylesheet Language Transformations (XSLT) Samples Viewer 1.0 is a visual, interactive learning tool that provides sample XSLT style sheets for XSLT elements and functions, as well as XPath functions. For each element or function, the viewer provides a common XML document and an XSTL style sheet. To see the results of applying the style sheet to the document, just click the Result button in the XSLT Samples Viewer.
Tuesday, August 26, 2008
SQL DMVStats
A SQL Server 2005 Dynamic Management View Performance Data Warehouse
Microsoft SQL Server 2005 provides Dynamic Management Views (DMVs) to expose valuable information that you can use for performance analysis. DMVstats 1.0 is an application that can collect, analyze and report on SQL Server 2005 DMV performance data. DMVstats does not support Microsoft SQL Server 2000 and earlier versions.
The three main components of DMVstats are:
• DMV data collection
• DMV data warehouse repository
• Analysis and reporting.
Data collection is managed by SQL Agent jobs. The DMVstats data warehouse is called DMVstatsDB. Analysis and reporting is provided by means of Reporting Services reports.
SQL Nexus Tool
SQL Nexus is a tool that helps you identify the root cause of SQL Server performance issues. It loads and analyzes performance data collected by SQLDiag and PSSDiag. It can dramatically reduce the amount of time you spend manually analyzing data.
Feature Highlights:
Fast, easy data loading: You can quickly and easily load SQL Trace files; T-SQL script output, including SQL DMV queries; and Performance Monitor logs into a SQL Server database for analysis. All three facilities use bulk load APIs to insert data quickly. You can also create your own importer for a custom file type.
Visualize loaded data via reports: Once the data is loaded, you can fire up several different charts and reports to analyze it.
Trace aggregation to show the TOP N most expensive queries (using ReadTrace).
Wait stats analysis for visualizing blocking and other resource contention issues (based on the new SQL 2005 Perf Stats Script).
Full-featured reporting engine: SQL Nexus uses the SQL Server Reporting Services client-side report viewer (it does not require an RS instance). You can create reports for Nexus from either the RS report designer or the Visual Studio report designer. You can also modify the reports that ship with Nexus using either facility. Zoom in/Zoom out to view server performance during a particular time window. Expand/collapse report regions (subreports) for easier navigation of complex data. Export or email reports directly from SQL Nexus. Nexus supports exporting in Excel, PDF, and several other formats.
Extensibility: You can use the existing importers to load the output from any DMV query into a table, and any RS reports you drop in the Reports folder will automatically show up in the reports task pane. If you want, you can even add a new data importer for a new data type. SQL Nexus will automatically “fix up” the database references in your reports to reference the current server and database, and it will provide generic parameter prompting for any parameters your reports support.
Monday, August 25, 2008
NetBeans
The only IDE you need! Runs on Windows, Linux, Mac OS X and Solaris. NetBeans IDE is open-source and free.
Sunday, August 24, 2008
Desktops
By Mark Russinovich and Bryce Cogswell
Published: August 21, 2008
Introduction
Desktops allows you to organize your applications on up to four virtual desktops. Read email on one, browse the web on the second, and do work in your productivity software on the third, without the clutter of the windows you’re not using. After you configure hotkeys for switching desktops, you can create and switch desktops either by clicking on the tray icon to open a desktop preview and switching window, or by using the hotkeys.
.png)
.png)
Download Desktops
(62 KB)
Run Desktops now from Live.Sysinternals.com
CodeProject: VbScript Editor With Intellisense.
VbScript Editor With Intellisense

Download ScriptEditor.zip - 349.9 KB
Ping in VB.NET 2005 with Async method using multiple IP's
Private mPingAddresses As List(Of String)
Private Sub Form1_Load(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles MyBase.Load
mPingAddresses = New List(Of String)
' Initialise the list of addresses...
mPingAddresses.Add("10.0.0.110")
mPingAddresses.Add("10.0.0.128")
mPingAddresses.Add("10.0.0.197")
mPingAddresses.Add("192.168.1.1")
mPingAddresses.Add("192.168.1.2")
mPingAddresses.Add("192.168.0.2")
End Sub
Private Sub Button1_Click(ByVal sender As System.Object, ByVal e As System.EventArgs) Handles Button1.Click
' Clear any existing items
Me.ListBox1.Items.Clear()
' Loop through the addresses generating an aysnc ping...
For Each ipAddy As String In mPingAddresses
' Generate the request
Dim myPing As New Net.NetworkInformation.Ping()
' Add the handler for this request...
AddHandler myPing.PingCompleted, AddressOf PingRequestCompleted
myPing.SendAsync(ipAddy, ipAddy)
Next
End Sub
Public Sub PingRequestCompleted(ByVal sender As Object, ByVal e As Net.NetworkInformation.PingCompletedEventArgs)
' When received, add the approrpiate entry into the listbox
Me.ListBox1.Items.Add(e.UserState.ToString & " " & e.Reply.Status)
End Sub
NetPing util
NetPing util
NetPing (and source) is now hosted on CodePlex in two sites: one for NetPing itself, and another for AddIns. The rest of this page is retained for historical record. Thanks for visiting!

NetPing (and source) is now hosted on CodePlex in two sites: one for NetPing itself, and another for AddIns. The rest of this page is retained for historical record. Thanks for visiting!
SingleDrive
SingleDrive
It's nothing fancy like a file system driver, but simply a Windows Explorer-like app that shows any number of drives and network shares as a single entity.
Features:
Display all of your local and network hard drives in a single view.
Search.
Delete files/folders. (Local files sent to the recycle bin, remote are deleted.)
View file/folder properties.
Open files.
Download

It's nothing fancy like a file system driver, but simply a Windows Explorer-like app that shows any number of drives and network shares as a single entity.
Features:
Display all of your local and network hard drives in a single view.
Search.
Delete files/folders. (Local files sent to the recycle bin, remote are deleted.)
View file/folder properties.
Open files.
Download
Saturday, August 23, 2008
Capture video thumbnails with Classic ASP using ffmpeg - Hiveminds Magazine
option explicit
dim sExecuteable
dim oShell
dim sVideoFilepath
dim sOutputFilepath
dim cmd
sExecuteable = "ffmpeg.exe"
sVideoFilepath = "sphere1.wmv"
sOutputFilepath = "sphere.png"
cmd = server.mappath(sExecuteable) & " -y -i """& _
server.mappath(sVideoFilepath) &""" -vframes 1 -an _
-vcodec png -f rawvideo -s 320x240 """&_
server.mappath(sOutputFilepath) &""""
set oShell = server.createobject("Wscript.Shell")
oShell.run cmd
set oShell = nothing
Wednesday, August 20, 2008
VB.NET - Den MD5 Hash einer Datei ermitteln
Visual Basic
Imports System.Security.Cryptography
Imports System.Text
Imports System.IO
Public Function MD5FileHash(ByVal sFile As String) As String
Dim MD5 As New MD5CryptoServiceProvider
Dim Hash As Byte()
Dim Result As String = ""
Dim Tmp As String = ""
Dim FN As New FileStream(sFile, FileMode.Open, FileAccess.Read, FileShare.Read, 8192)
MD5.ComputeHash(FN)
FN.Close()
Hash = MD5.Hash
For i As Integer = 0 To Hash.Length - 1
Tmp = Hex(Hash(i))
If Len(Tmp) = 1 Then Tmp = "0" & Tmp
Result += Tmp
Next
Return Result
End Function
Tuesday, August 19, 2008
XMLTextWriter & XMLTextReader - ASP Alliance
This article describes how to write pre-defined XML to a file by using XmlTextWriter class. XmlTextWriter provides a fast, forward-only way of generating XML documents without the overhead of a DOM. …
Subscribe to:
Posts (Atom)